Watch Out for Tax Scams!
It’s that time of year again: tax filing season. It can be really stressful! Unfortunately, there is usually a large jump in the number of tax scams at this time of the year. Cyber security experts have warned about the specific ways that cyber criminals steal sensitive, private information.
A month or so ago, the IRS released its “Dirty Dozen” list of tax scams for 2017.1 In this list, the IRS mentioned phone and phishing scams as serious threats.
Phishing is defined as “the attempt to obtain sensitive information such as usernames, passwords, and credit card details (and, indirectly, money), often for malicious reasons, by disguising as a trustworthy entity in an electronic communication.”2
sensitive information such as usernames, passwords, and credit card details (and, indirectly, money), often for malicious reasons, by disguising as a trustworthy entity in an electronic communication.”2
Basically, criminals pretend to be someone you trust in order to steal important financial and personal info. They use this information to log into peoples’ accounts, like bank accounts, to transfer funds. Also, they sell it to other criminals. Phishing can be done through phone calls, emails, texts and other communication forms.
Consumer Tax Scam Examples
Recently, criminals are using a number of different tax scams to attack consumers. They make calls or send emails, which appear to be from the IRS. Their emails ask the consumer to update missing information, pay an outstanding tax liability or receive a refund by clicking on a link. Their emails may also contain links to malicious websites, which appear to be IRS related and ask them to enter confidential info.
Criminals make calls and demand that consumers pay an outstanding tax balance. They threaten severe penalties if they don’t. Their scams have gotten very complex. In some cases when they have already stolen consumers’ personal and financial information, the criminals submit falsified tax returns. Then, they request that refunds be sent to consumers’ bank accounts. When the refunds are deposited, they call consumers and pretend to be IRS reps. They indicate that a refund was made mistakenly and demand that the consumer transfer this money to another account. Basically, they are involved in money laundering.
Tax Pro and Business Related Tax Scams
Often, criminals use some of the same techniques with tax pros (like accountants) as they do with consumers. Posing as IRS reps, especially from the e-Services department, they send phishing emails to tax pros asking them to click on a link to sign into their accounts. However, the link brings them to a fake e-Services site that steals usernames and passwords. Sometimes, the criminals will send emails tax with attachments containing malware. Once they click on the attachments, the software will load which tracks their keystrokes.
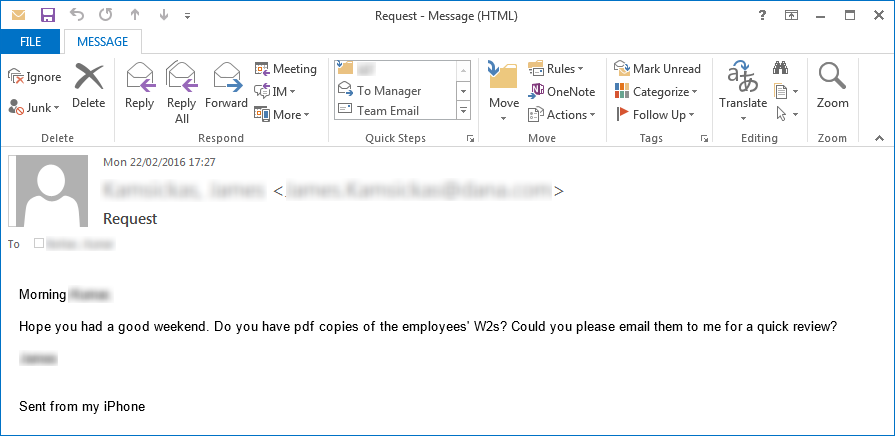
On the business side, cyber criminals pose as company executives and send emails to HR reps demanding employee W-2’s. Once the HR reps reply with the requested info, the criminals have everything they need to file false tax returns.
Realizing these serious threats, we outlined five ways consumers, tax pros and businesses can protect themselves from tax scams.
5 Ways to Protect Your Info from Tax Scams
Use a Secure Internet Connection
When you login into any account containing sensitive info or submit a tax return online, make sure that you are on a private, password protected network. Don’t ever file taxes or access important information while on a public Wi-fi at Starbucks or the airport. Instead of clicking on email links, manually type in any website address. Also, make sure the website you connect with has a “https” in the URL and you see a lock symbol in the address bar.
Encrypt Email and Documents
If you are a tax professional, you should be using encrypted email and documents. When you send an email, cyber criminals can access its contents at several points during its transmission. Encryption helps to prevent people hacking into your email account and hides the email’s content from unwanted parties. Many email services, like Microsoft Office 365, offer the option of encrypted email.
In addition to encrypting emails, you can also encrypt documents to make sure the criminals do not access them. In order to access a file or folders, you will need to enter a password. Microsoft Windows comes with software (Bitlocker) to do this. Also, there is commercial software (Symantec Endpoint Protection) which will protect docs. Instead of individual files or folders, you can protect entire drives.
Implement Proactive Monitoring and Maintenance Through a Trusted IT Partner
These services will make sure that your computer Operating Systems and software are automatically updated. This will help keep your systems are secure and protected. A trusted IT partner should be aware of the most recent threats and take steps to prevent them.
Use a Professional Firewall and Commercial Anti-virus
By installing a physical and software firewall, you create a barrier to your network from the outside world. Professional firewalls, like Sonicwalls, look for any unusual inbound or outbound network traffic. They also have anti-virus and anti-malware software which will scan your network for unwanted things. In addition to a network firewall which would be an outer barrier, each computer should have its own software firewall to scan and potentially block anything which gets into your network.
While a free anti-virus may protect your systems against certain attacks, like virus infections, it may not properly protect you against certain malware. We recommend commercial software, like Webroot, to protect your systems.
Establish Clear Business Security Policies and Procedures
A business should have specific security policies and procedures in place and communicate them clearly to employees. For instance, every business should have a specific policy for managing users’ passwords. It should make sure that everyone uses strong, unique passwords with two-factor authentication. A business should require that passwords be changed every 30 – 60 days.
Every business should also educate employees on the different email and phone scams they could face, especially tax related ones. It should have specific procedures what employees should do when they receive a suspicious email or call. For instance, employees should never open an attachment to an email that discusses tax information.2
Additional Safety Tips
To make sure you and your business are as safe as possible, we included some additional safety tips:
- When you receive a suspicious email or call, go directly to the source. If your manager asks for W2’s by email, call him or her to verify.
- If you file by regular mail, send the documents directly from the post office or a UPS/FedEx site. Do not leave your tax documents in your mailbox. Criminals could steal them.
- Run regular virus/malware scans on your PCs.
- Schedule quarterly security meetings at your business. Regularly check that everything is in place to make your business as secure as possible
References:
- IRS.gov “IRS Summarizes “Dirty Dozen” List of Tax Scams for 2017.” Link to Site
- Wikipedia “Phishing.” Link to Article
- Applied Synergy Group “5 Ways to Securely File Your Income Tax Return.” Link to Article