Smartphone Hacking on the Rise
Do you know that there are about 230 million US smartphone users and over 2 billion worldwide? Do you know that U.S. smartphone users spend about an hour and half each day on their phone? For many of us, smartphones have become integral part of our daily lives. Besides using them for email and making calls, we use them to do just about anything: banking, accessing social media and taking photos. This means that smartphones can hold some really important personal and financial information.
Because the smartphone market is so large and these devices hold such valuable information, hackers have become increasingly focused on breaking into them. Recently, there has been a large increase in smart phone hacking. In the future, we expect the attacks to only get worse.
Recognizing these threats, we wrote an article about the five ways individuals can make their phones more secure and reduce the chances of being hacked.
 Application Download and Installation
Application Download and Installation
The first step you can take to better protect your smartphone is to be extremely careful about what you are downloading and installing. The best rule of thumb is to only download apps from the Apple App store or the Google Play Store and not unofficial sites.
Apple does a great job of screening which apps become available through its App store. You can be confident that the applications you install on your iPad or iPhone are free of malware and viruses. The apps on the Google Play Store are more likely to have malware or viruses, but usually you can be confident when downloading from their store. Google has a scanner which scans its Play Store for malicious apps.
Also, it is important to check the permissions a new app is requesting when you download it. If a flashlight app is asking for permission to access your contacts, this should be a red flag.
Disable Bluetooth 
When you can, we recommend that you disable bluetooth. Some hackers have used bluetooth to break into smartphones. There are different bluetooth versions with varying levels of security. The older versions have more security holes, while newer versions have become more secure. In general, it is best to disable bluetooth when you don’t need it.
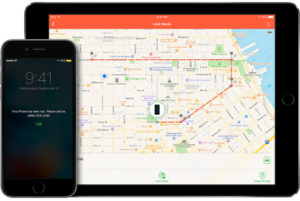 Enable Device Finder and Remote Wipe
Enable Device Finder and Remote Wipe
If your smartphone is stolen, you want to be able to remotely track it and to delete it. On the iPhone, you can enable “Find my iPhone” under the “iCloud” settings. If your device disappears, you can put it in lost mode. This locks your screen with a pass code. You can display a custom message to help you get it back. You can also delete everything on your iPhone, so your personal information cannot be accessed. For Android devices, you can remotely locate, lock and wipe your phone by using the Android device manager and third party apps.
 Enable Encryption
Enable Encryption
While the iPhone comes with full-disk encryption automatically enabled, you will have to enable encryption on Android phones. Basically, the encryption protects your data by requiring a password for someone to be able to access your information in a usable form. Without that password, it would be extremely difficult to hack it.
To set up encryption on an Android, you would need to go into “Security” in the Android settings and select “Encryption.” It may take an hour or two to encrypt the device. Then, after this you will be asked to enter this password every time your Android device boots up.
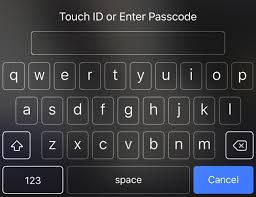 Use a Pass Code
Use a Pass Code
Your phone should be set to immediately lock when not in use. It is very important to set a pass code or biometric (finger print, face recognition, etc.) security to protect it. If you are using a pass code, the longer the better. If your code is six digits long, this will make it 100 times more secure than a usual four digit one.
There are locking settings you can change to increase your smartphone’s security. For instance, immediate locking will ensure that it will be hard to access your important information. Don’t set your phone to lock after one minute or so. Also, you can set your phone to erase all data after a certain number of failed entry attempts.
Related References:
CNBC.com “Your Smart Phone could be hacked without your knowledge”: Link to Article
The New York Times “With Wikileaks Claims of C.I.A Hacking, How Vulnerable is Your Smartphone?”: Link to Article
Cnn.com “WikiLeaks CIA hacking claims: How worried should you be?”: Link to Article



